Homepage
SPHERE RESEARCH INFRASTRUCTURE
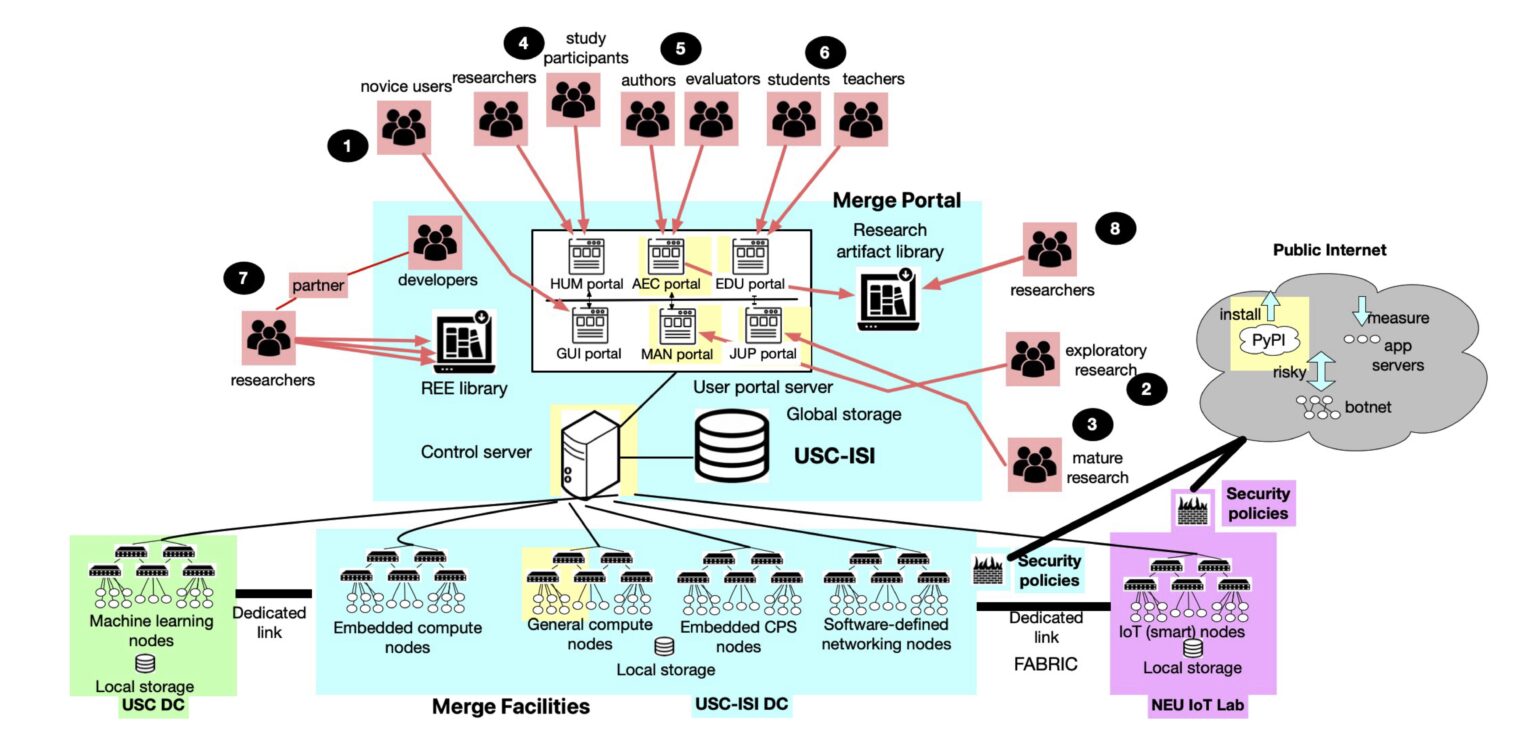
SPHERE (Security and Privacy Heterogeneous Environment for Reproducible Experimentation) is a national research testbed funded by the NSF that supports integrated, reproducible cybersecurity and privacy research through access to diverse, user-configurable hardware, software, and networking resources via six specialized user portals. It aims to transform cybersecurity and privacy research, enabling representative, sophisticated, and reproducible experimentation that allows researchers to build on the work of their peers, thus supercharging scientific progress. In addition to scientific experimentation, SPHERE enables a broad range of activities including education, workforce training, cybersecurity exercises, and rigorous test and evaluation.





GETTING STARTED WITH SPHERE
While the SPHERE infrastructure is still undergoing construction, it is open to beta users using currently available resources. To begin using SPHERE, click the “Register” button in the top-right corner of the homepage to create an account; returning users can log in via the adjacent “Login” button. Once approved, you can begin designing and running experiments using SPHERE’s intuitive interfaces and configurable infrastructure. The platform also provides user guides, tutorials, and community support to help you make the most of its capabilities.
Researchers, educators, students, and industry partners can collaborate with SPHERE by contributing experiment artifacts, participating in community workshops, or integrating SPHERE into academic courses, training programs, or cybersecurity exercises.
HOW SHOULD I CITE SPHERE?
If you use SPHERE in your research and a publication, we would appreciate a citation. Currently, the best reference for SPHERE is:
Jelena Mirkovic, David Balenson, Brian Kocoloski. Enabling Reproducibility through the SPHERE Research Infrastructure. USENIX ;login: Online, USENIX Association. December 16, 2024. https://www.usenix.org/publications/loginonline/enabling-reproducibility-through-sphere-research-infrastructure
CALL FOR REES NOW CLOSED!
The SPHERE research infrastructure aims to improve transparency and reusability of research artifacts, enabling others to more easily build on prior work. To support this goal, selected contributors of Representative Experimentation Environments (REEs) received paid virtual internships to port their work into SPHERE, expanding accessibility and ensuring long-term impact. If you missed this year’s opportunity, be sure to check back when we reopen applications for Summer 2026.
SUMMER 2025 INTERNSHIP APPLICATIONS NOW CLOSED!
Thank you to all the students who applied for the SPHERE Summer 2025 internships! If you missed this opportunity, be sure to check back next year when we open applications for Summer 2026. Click 'Student Internships' for more information.
PLEASE TAKE OUR COMMUNITY NEEDS SURVEY
We are running a survey to learn about researcher needs around cybersecurity and privacy experimentation. Your feedback will inform our future endeavors in supporting cybersecurity experimentation through our recently funded SPHERE research infrastructure. We want to hear from a wide range of researchers, no experience is too small. The form has six open-ended questions, it is anonymous and you can skip any questions.










